1. Sample overview
Hash: af6a9b7e7aefeb903c76417ed2b8399b73657440ad5f8b48a25cfe5e97ff868f
In this new sample, threat actor has updated Qakbot’s codebase to support 64-bit versions of Windows.
(more…)Hash: af6a9b7e7aefeb903c76417ed2b8399b73657440ad5f8b48a25cfe5e97ff868f
In this new sample, threat actor has updated Qakbot’s codebase to support 64-bit versions of Windows.
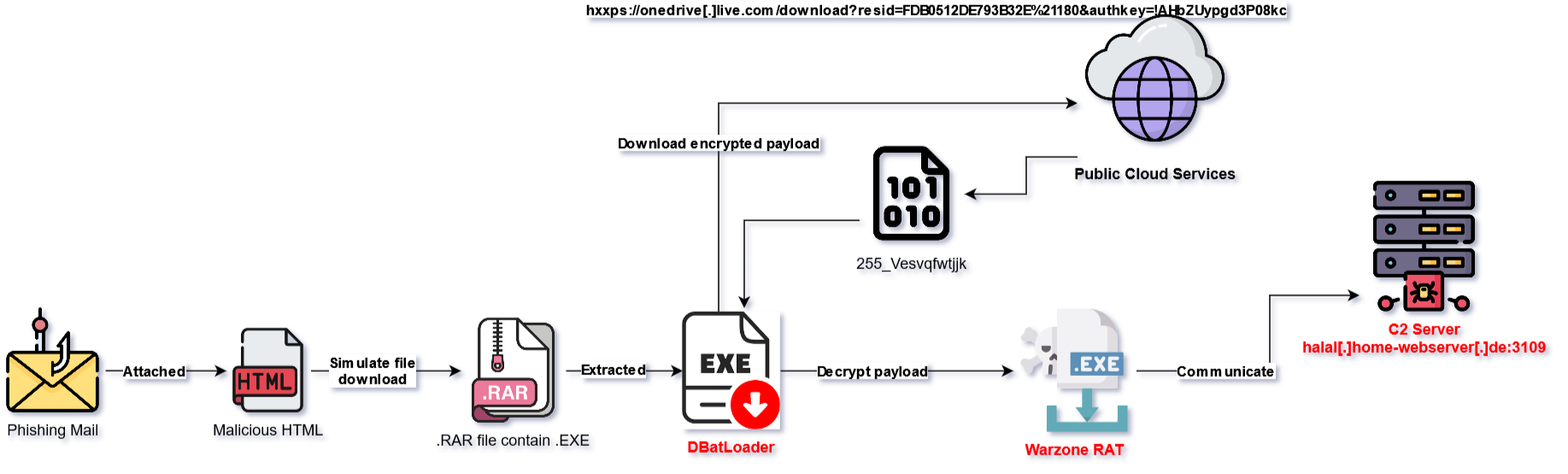
(more…)Below is an illustrated and summarized way of how WarZone RAT sample infects the victim system via DBatLoader:
In early February 2023, cybersecurity experts on Twitter issued a warning about a new malware variant/family being distributed by the #TA577 botnet (associated with the same group from #Qakbot). This malware shares similarities with the Qakbot Trojan, including distribution methods, campaigns, and behaviors. It was quickly nicknamed Pikabot.
Pikabot consists of two components: loader/injector and core module. It utilizes loader/injector to decrypt and inject the core module. Core module then performs malicious behaviors, including gathering information about the victim machine, connecting to command and control server to receive and execute arbitrary commands, downloading and injecting other malware.
(more…)I would like to share my presentation at the Security Bootcamp 2023 (SBC2023) event, which took place over three days from September 8th to September 10th, 2023, in Da Nang city.
2023 is the 10th anniversary of Security Bootcamp, and the second time was held in Da Nang city. The event continues its mission of building and connecting the community of cybersecurity professionals nationwide to share the latest knowledge and skills, creating a reputable and quality conference for cybersecurity in Vietnam.
(more…)The attacker sent an email with an attachment named “brochure-for-2023-elite-events.rar”. This rar file contains only one lnk (shortcut) file named: brochure-for-2023-elite-events.pdf.lnk. If the user does not pay attention and extracts the file, it will be displayed as a PDF icon like the following: