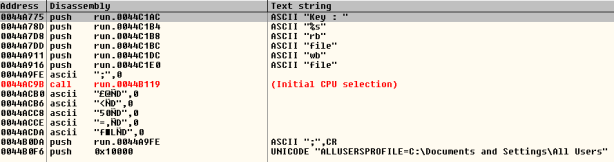
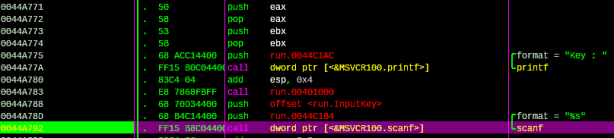
1.1. First solution
Rule in Readme.txt:
-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=- AuthKey = un_md5(DecryptKey) + " " + un_md5(EXE's Key) -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=- Ex:) DecryptKey = 1dfb6b98aef3416e03d50fd2fb525600 EXE's Key = c944634550c698febdd9c868db908d9d => AuthKey = visual studio -=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-
Scan this target by ExeInfo PE:

Figure 1
We have “AutoHotkey v1.0.48.05 – AutoIt3 v2.x.x” and ExeInfo recommend us use Exe2Aut to Unpack/Decompile this target. Ok, let’s try to use ExeInfo and here is the result:

Figure 2
Open _myExeToAut.log in the same directory, we will have the first MD5 key “220226394582d7117410e3c021748c2a”
================================================================================
-= myExe2Aut >The Open Source Autoit/AutoHotKey Script Decompiler< 1.92 build(54) =- ================================================================================ Unpacking: C:\Documents and Settings\manowar\Desktop\Reversing.kr\Chal13\ahk.exe AU3_Signature: A3 48 4B BE 98 6C 4A A9 99 4C 53 0A 86 D6 48 7D £HK¾˜lJ©™LS †ÖH} Script Type 3.0 found. 00032813 -> SubType: 0x03 áú
~ Note: The following offset values are were the data ends (and not were it starts) ~
Script is password protected!
00032834 -> Password/MD5PassphraseHash: 3232303232363339343538326437313137343130653363303231373438633261
220226394582d7117410e3c021748c2a
MD5PassphraseHash_ByteSum: 0000075D '+ 22AF' => decryption key!
Open another file is ahk.ahk, we get the second key “54593f6b9413fc4ff2b4dec2da337806”:
;<COMPILER: v1.0.48.5>
inputbox,pwd
if (pwd== "54593f6b9413fc4ff2b4dec2da337806"){
MsgBox
}
Open https://hashkiller.co.uk/md5-decrypter.aspx to decrypt above MD5 keys:

Figure 3

Figure 4
Finally, the right Flag is: isolated pawn
1.2. Second solution
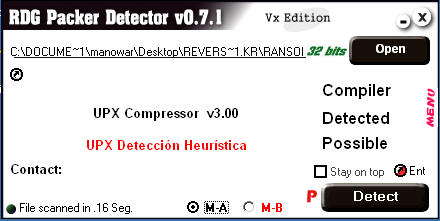
Scan this target by RDG Packer Detector:

Figure 5
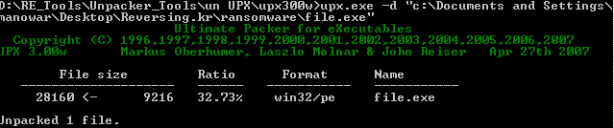
RDG shows this target is packed by UPX. Let’s try to use UPX to unpack:

Figure 6
Run unpacked file, we get the error messages:

Figure 7
Let’s open OllyDBG and load packed file, scroll down and put BP at “00471BD9 ^\E9 710FFDFF jmp ahk.00442B4F” to manual unpack it:

Figure 8
F9 to run, we stop at BP. F8 to trace over, we stop here:

Figure 9
Search all referenced text strings to find “EXE corrupted”:

Figure 10
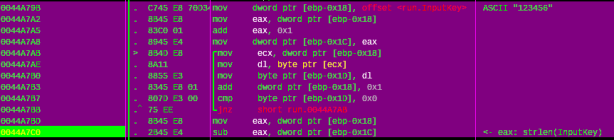
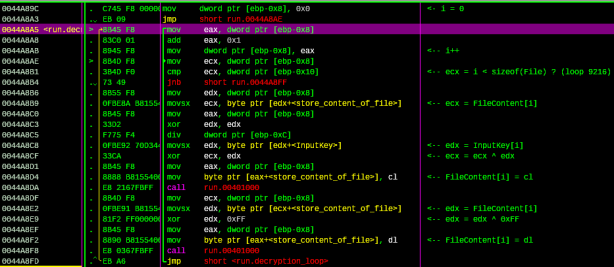
Double click on the ASCII “EXE corrupted“, we go to the following address: 0x00448273. Scroll up, we can see the jump that will bypass the error message at “00448265 |. /74 16 je short ahk.0044827D”. So we need to place a breakpoint at the call before this jump:

Figure 11
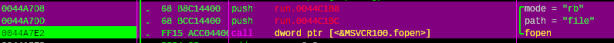
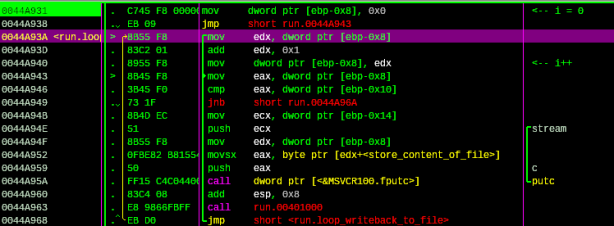
Then press F9, we’ll stop at bp. Press F7 to trace into this call, then F8 to trace over, the routine will show us the address that store the decryption key:

Figure 12
After finish the call at “0044825E |. E8 64860000 call ahk.004508C7 ; \ahk.004508C7”, we back to the jump that will bypass the the error message at “00448273 |. 68 34E34500 push ahk.0045E334 ; ASCII "EXE corrupted"” and stop here:

Figure 13
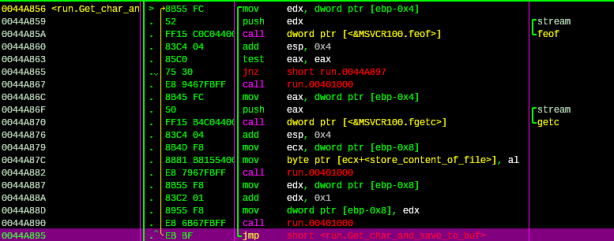
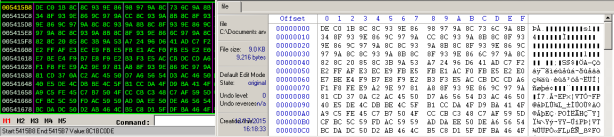
This routine will decompile the file with the decryption key above. After trace over the call at address “00448293 |. E8 078A0000 call ahk.00450C9F ; \ahk.00450C9F” and follow in dump the address at ECX register, we’ll have the exe’s key:

Figure 14
Finally, visit https://hashkiller.co.uk/md5-decrypter.aspx to decrypt above keys that we get!
End.